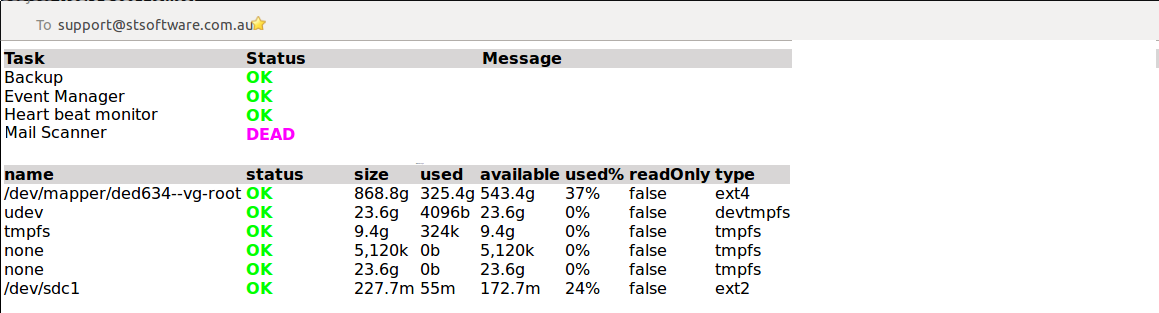
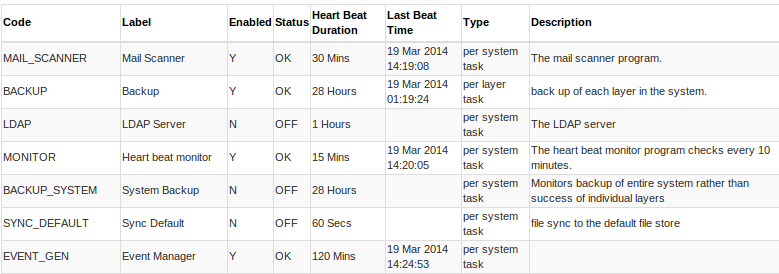
Overview
A new responsive design for the main control panel.
Features include:-
- Responsive design
- Search box now searches articles.

-
- Latest emails
- Open tasks
- Alerts
- Password change, settings & log out
- Alert Menu
- Search Articles
Try out the Demo
- 26 Mar 2014
Overview
Our free text shorter service uses a clever combination of word replacement, adorable images and good old fashioned magic to optimize your tweets. In case you don't have hours to sit with your teenager to learn the latest hipster abbreviations this service is for you.
- 25 Mar 2014
Overview
Best practice network design for a highly scalable, distributed web system has:-
-
- No single point of failure.
- Fault tolerant
- Servers are locked down
- Defence in depth
- Load balancing
- Lowest possible permissions/access for each component
- Health monitoring for each component
- 21 Mar 2014
SQL injection is a code injection technique, used to attack data driven applications like stSoftware.
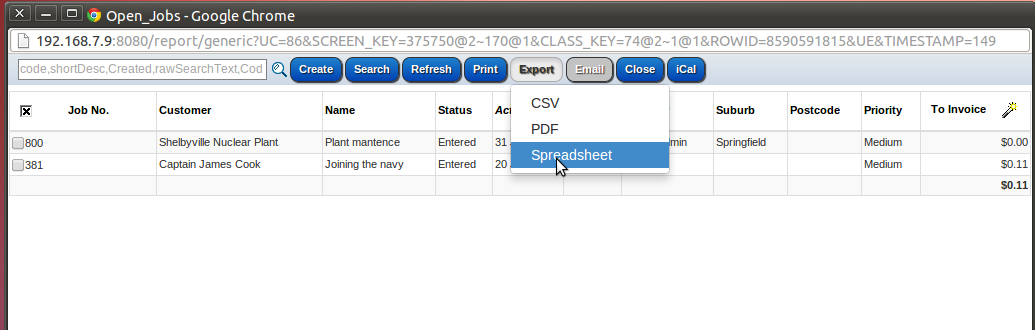
stSoftware systems support a number of web accessible protocols including:-
- ReST
- SOAP
- Web Forms
- GWT RPC
All protocols access the underlying data through the DAL ( data access layer). There is NO direct access to the underlying data store no matter which protocol is used. Each protocol accepts the request to read or write data and then perform the protocols validations and then passes the request on to the DAL to execute the request which in turn validates the request, checks the user's access and perform any validations before returning the result.
SQL & XSS attacks are automatically tested for each of the supported protocols. Listed below are the standard SQL injection strings attempted.
| SQL Injection String |
| "&%00<!--\'';你好 |
| \'; DROP |
- 14 Mar 2014
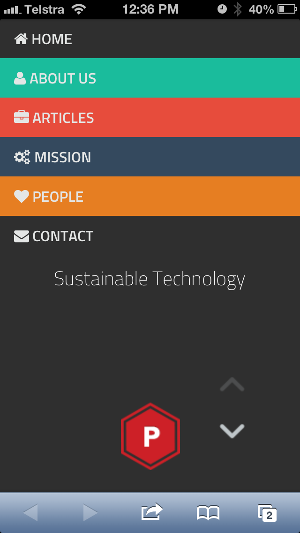
A new template "Munter" has been added to our Content Management System (CMS). Munter is a very handsome Bootstrap 3 theme. Comes with beautiful features like a fixed arrows navigation, a nice portfolio showcase and a smooth scroll.
- Sections:-
- All site details can be updated via the site wizard
Home page - mobile
- 7 Mar 2014
Overview
Single sign using Microsoft LAN Manager (NTLM) allows users within a intranet enviroment to use the system without the need to re-enter their password once they have logged into the Windows network.
Note the NTLM protocol can only be used within a internet environment.
- 2 Mar 2014